
Deepfakes in the Boardroom: Why Governance Beats AI Detection
Deepfake attacks threaten businesses. Technical detection isn't enough. Resilient processes and clear governance structures are key to effective defense.

What does a Virtual CISO cost? Pricing, models, and comparison 2026
Transparent overview of vCISO pricing models: retainer, hourly, and project-based. With cost comparison to an internal CISO and decision guide for mid-sized companies.

When Clicks Disappear: How AI Threatens Information Diversity
AI snippets and platform answers drain traffic from content creators, creating a strategic risk for information supply in mid-sized businesses.

Logs in Ransomware Attacks: Why Server Failure Costs Millions
Encrypted servers, lost logs, and €400,000 in damages. Why proper log management strategies determine business survival during cyber attacks.

Incident Response: Who Decides in an Emergency?
Clear decision-making processes during security incidents are often missing in SMEs. Why this is a leadership issue and how to solve it.

MoltBot Tested: Why AI Agents Are a Security Risk
Open-source AI agents like MoltBot promise automation but pose significant security risks. A hands-on test reveals what businesses must consider.

Shadow AI in Mid-Market: Why AI Bans Fail
AI bans don't create security, they drive usage underground. How mid-market companies can manage Shadow AI through smart governance strategies.

Governance as Bullshit Filter: AI & Cyber Decisions
How structured governance helps you see through vendor hype and pseudo-solutions to make resilient decisions in AI and cybersecurity.
AI-Powered Cyberattacks: Why Defense Needs a Strategic Rethink
AI agents automate exploit development at industrial scale. How CISOs must adapt their defense strategy for scalable attacks.
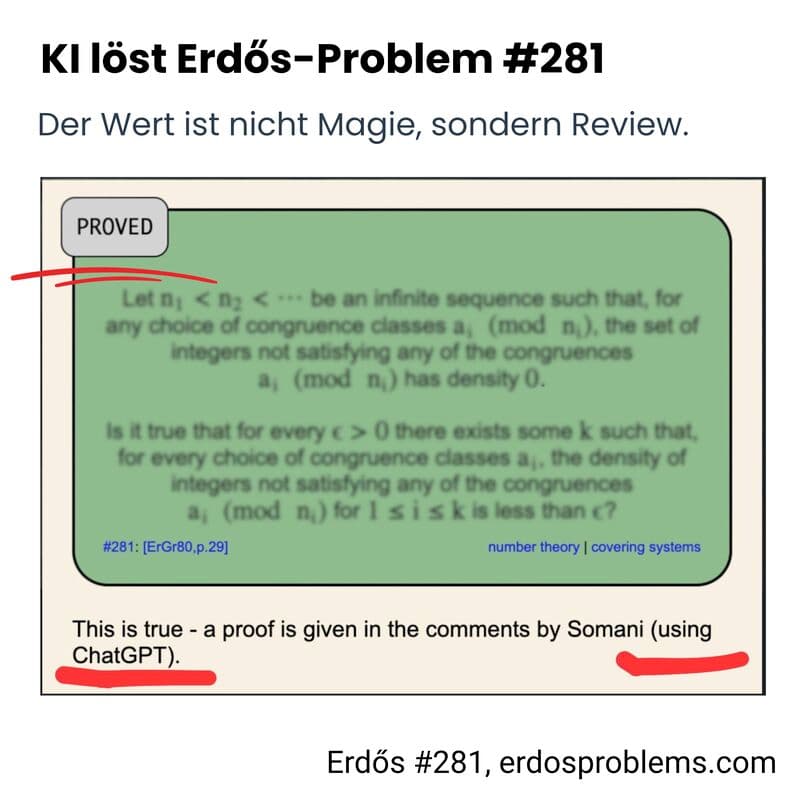
AI Governance: Why Process Beats Brilliance
AI solves complex problems not through genius, but through structured processes. How to use AI productively and verifiably.

AI in SMEs: Why Efficiency Without Control Creates Liability
Unchecked AI use becomes a liability risk. Three cases show why governance matters and plausibility doesn't equal truth in business.
AI Liability in SMEs: Governance Instead of Control
Rejecting AI doesn't increase control, it reduces transparency. Real security comes from smart governance, not manual work.
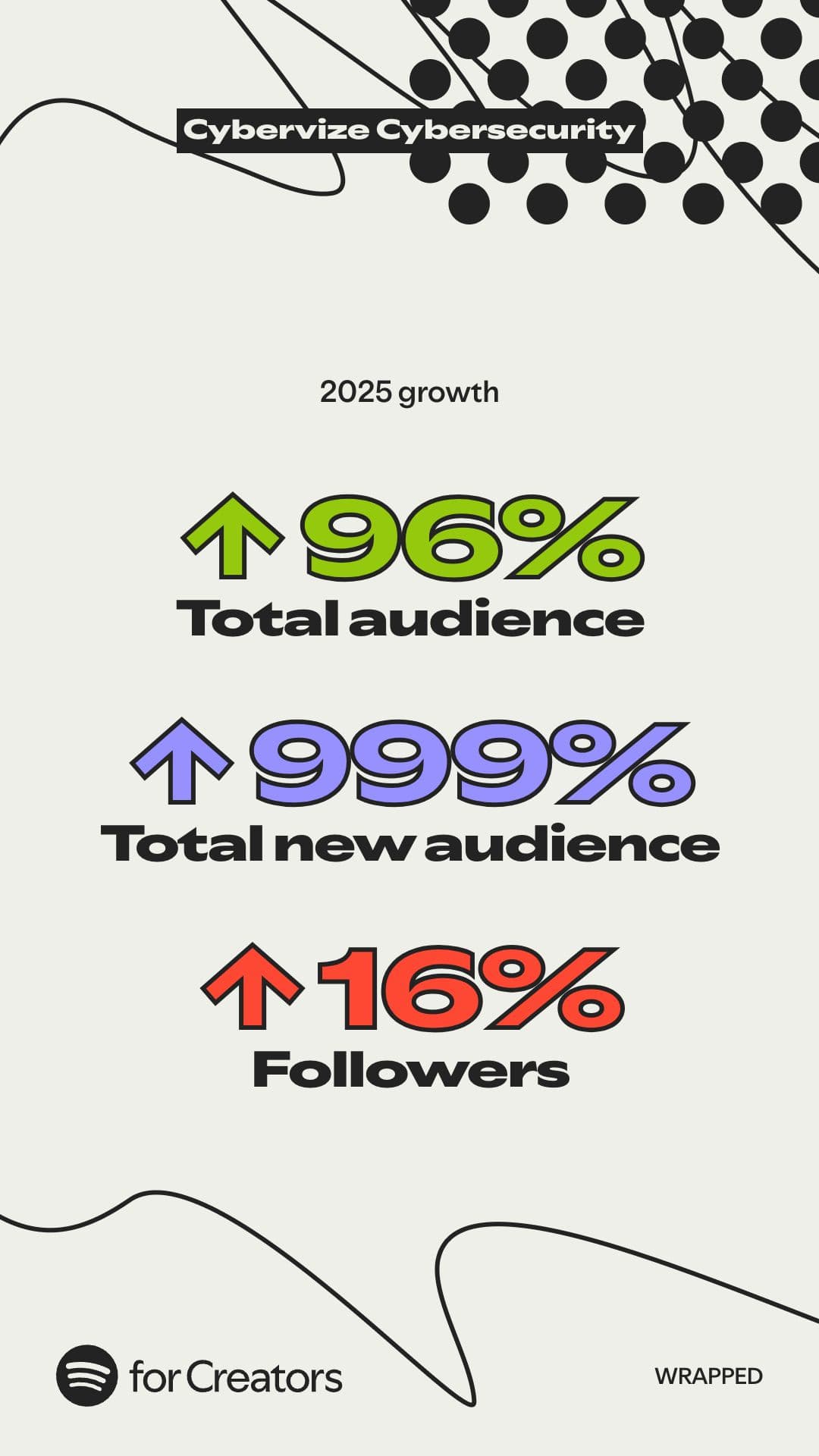
Cybervize Podcast 2025: Cybersecurity Made Accessible
The Cybervize Podcast grew 96% in 2025, making cybersecurity accessible to SMEs. Practical insights without buzzwords, for everyone.

CISO vs. CEO: Who's Accountable for IT Security?
The role distribution between CISO and CEO determines cybersecurity success. Learn who's truly accountable for IT security in your organization.

Cybersecurity is Leadership, Not Another Tool
German companies lose billions to cyberattacks because they treat security as a tool issue instead of a leadership responsibility.
US CLOUD Act & FISA 702: Why US Cloud Providers Are Problematic
US authorities can access data stored with American cloud providers, even when hosted in the EU. What does this mean for your business?

Cyberattacks: Hidden Costs for Balance Sheets and Stock Prices
New study reveals: 70% of companies lower forecasts after cyberattacks, 31% lose up to 10% of annual revenue. Cybersecurity is a C-level priority.
AI-Powered Cyber Attacks: How SMEs Can Protect Themselves
Artificial intelligence is automating cyber attacks. Learn how mid-sized companies can respond proactively with NIS2-compliant security management.

NIS2: Building the Bridge Between Compliance and Technology
How the gap between compliance and IT creates "alibi security" and why NIS2 demands a translator to bridge both worlds.

NIS2 Implementation Act Passed: What You Need to Do Now
Germany's Bundestag passed NIS2. Transition periods are minimal. Companies must act now to ensure compliance and avoid personal liability for management.

AI as Hacker: Why Security Culture Matters More Than Ever
Artificial intelligence is revolutionizing cyberattacks. Discover why human-centric security culture is now your best defense strategy.

Cybersecurity Tool Chaos in SMEs: The Process-Driven Approach
The cybersecurity market overwhelms SMEs with tools. Learn why a process-driven approach beats tool chaos and delivers NIS2 compliance faster.

GraphRAG in Cybersecurity: Explainable AI for Mid-Market Companies
How GraphRAG solves the AI black box problem and makes cybersecurity decisions transparent, traceable, and audit-ready.

Cybervize Pitch Day Berlin: AI Cybersecurity Meets Investors
A founder presents his AI-powered cybersecurity platform to investors in Berlin and shares insights into the vibrant startup community.

Human Risk Management: Safety-I vs. Safety-II in Cybersecurity
Why true cyber resilience needs more than lower click rates: The difference between behavior control and systemic security.

GraphRAG: Transparent AI for Enterprise Applications
GraphRAG offers a secure alternative to simple AI wrappers. Learn how graph-based AI integrates proprietary knowledge while ensuring compliance.

Jaguar Land Rover Cyberattack: Lessons for CISO and C-Level
The JLR cyberattack reveals why cyber insurance fails and what concrete measures companies must take now to remain insurable and resilient.

Vibe Hacking: Protect Your Business from AI-Powered Cyber Attacks
AI-powered cyber attacks threaten SMEs: Learn how systematic risk management and NIS2 compliance protect your business from emerging threats.

Cybersecurity Reporting for the Board: Decisions Instead of Tech
Effective cybersecurity reporting translates risks into business language and delivers concrete action options instead of technical jargon for strategic decisions.

Cybersecurity as a Team Sport: Shared Responsibility in Business
Cyberattacks require company-wide collaboration to defend against. Learn how every department contributes to security resilience.
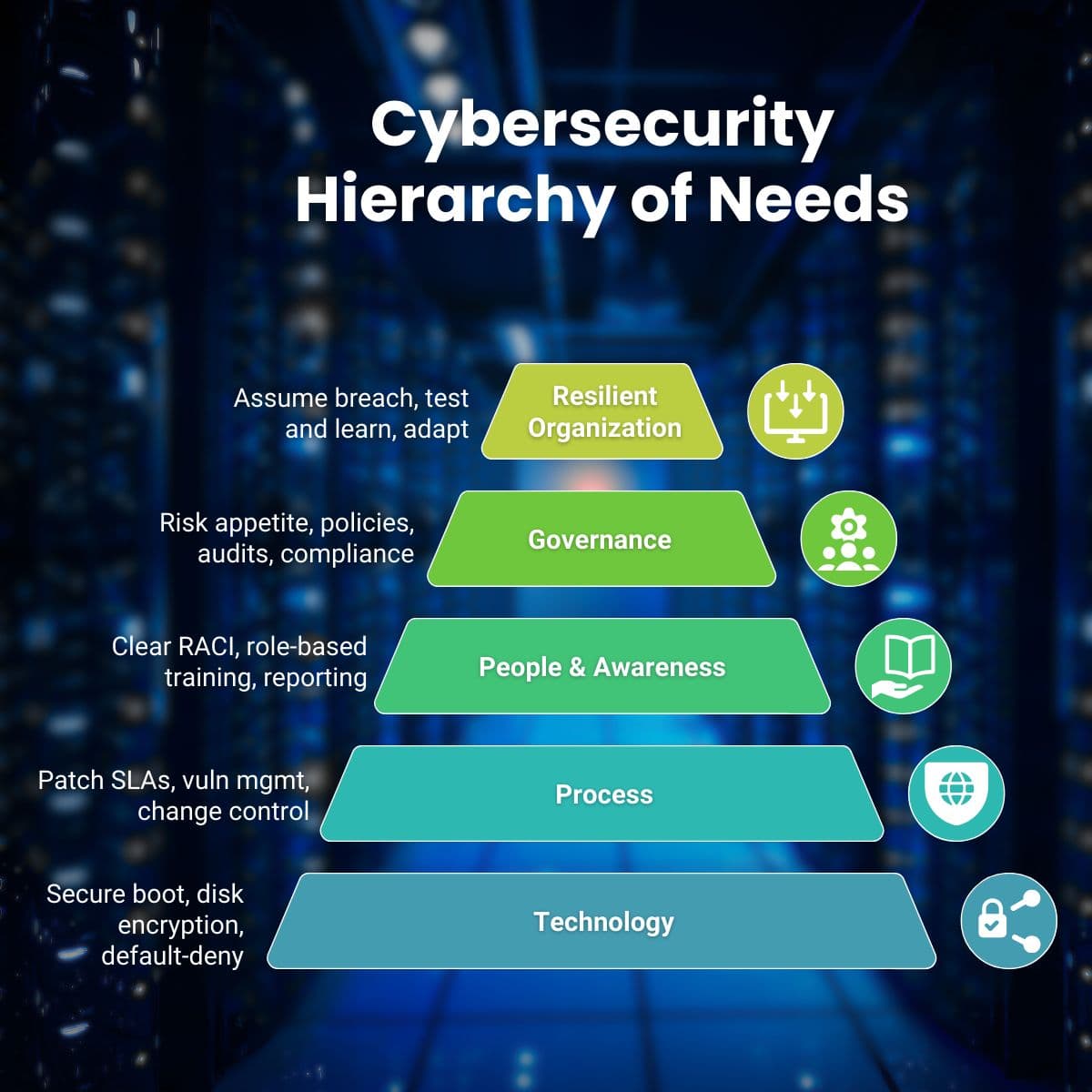
Maslow's Hierarchy Applied to Cybersecurity Strategy
Why the wealthiest companies get breached and how Maslow's hierarchy reveals the path to sustainable cyber resilience.

Email Security 2025: Why It's a Leadership Responsibility
Emails are the biggest security risk for SMEs. Learn why email security is not an IT task but a leadership responsibility.

Vibe Hacking: How AI Challenges Cybersecurity
AI-powered attacks are fundamentally changing the threat landscape. Companies must rethink cybersecurity as strategic risk management.

Risk Analysis in Cybersecurity: No Success Without a Plan
Methodical risk analysis is the foundation for effective cybersecurity. Learn how to set priorities and allocate budgets strategically.

Cybersecurity in SMEs: Management Over Tool Chaos
82% of companies report increased cyberattacks. Why tools alone aren't enough and how management systems with Virtual CISO create solutions.

Cybersecurity in SMEs: Management over Tools
82% of companies report more cyberattacks. Why governance and processes matter more than new tools and how Virtual CISOs help.

Cybervize at Cyber Investor Days 2025 in Bochum
Meet Cybervize on September 10 in Bochum: ISMS SaaS for NIS2, ISO 27001, and IT-Grundschutz. Investor meetings available.
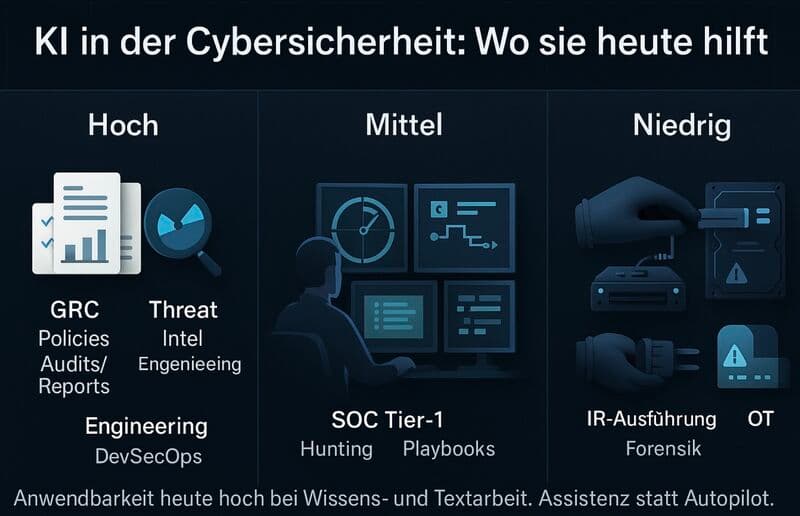
AI in Cybersecurity: Where It Really Helps
AI supports CISOs in GRC, threat intelligence, and DevSecOps. But critical decisions remain human. A practical overview.

Compliance in Cybersecurity: Design over Drama
Why modern compliance protects through smart system design rather than click marathons and fear culture. Practical examples for effective security.

The Coming Wave: How AI Transforms Cybersecurity Forever
Mustafa Suleyman's "The Coming Wave" reveals how AI makes cyberattacks faster and more precise. Companies must fundamentally rethink their security strategies now.
Cybersecurity Needs Leadership: Why Tools Alone Aren't Enough
More security tools don't equal more security. Without clear governance and leadership, you create an expensive patchwork attackers easily exploit.

NIS-2 is Coming: Roadmap & 10-Minute Check for Companies
The NIS-2 directive becomes reality in 2025. Check in 10 minutes if your company is affected and avoid fines of up to 2% of revenue.

The 95% Myth: Why Blame Games Hurt Cybersecurity
Cyber incidents aren't just human error. Technology, processes, and people form an attack chain that requires holistic solutions, not blame.
