Maslow's Hierarchy Applied to Cybersecurity Strategy
How Maslow Solved Your Cyber Strategy in 1943
If technology solved security problems, the wealthiest companies would never fall victim to cyberattacks. Yet reality tells a different story: despite million-dollar budgets and cutting-edge security tools, we regularly witness spectacular data breaches at major corporations. Why is that?
After years of conversations with CEOs and board members, I've repeatedly tried to explain why buying more dashboards and monitoring tools doesn't repair fragile foundations. Then came the realization: Abraham Maslow already solved this problem in 1943. His hierarchy of needs shows that higher goals collapse when basic needs aren't met. This principle translates directly to cybersecurity.
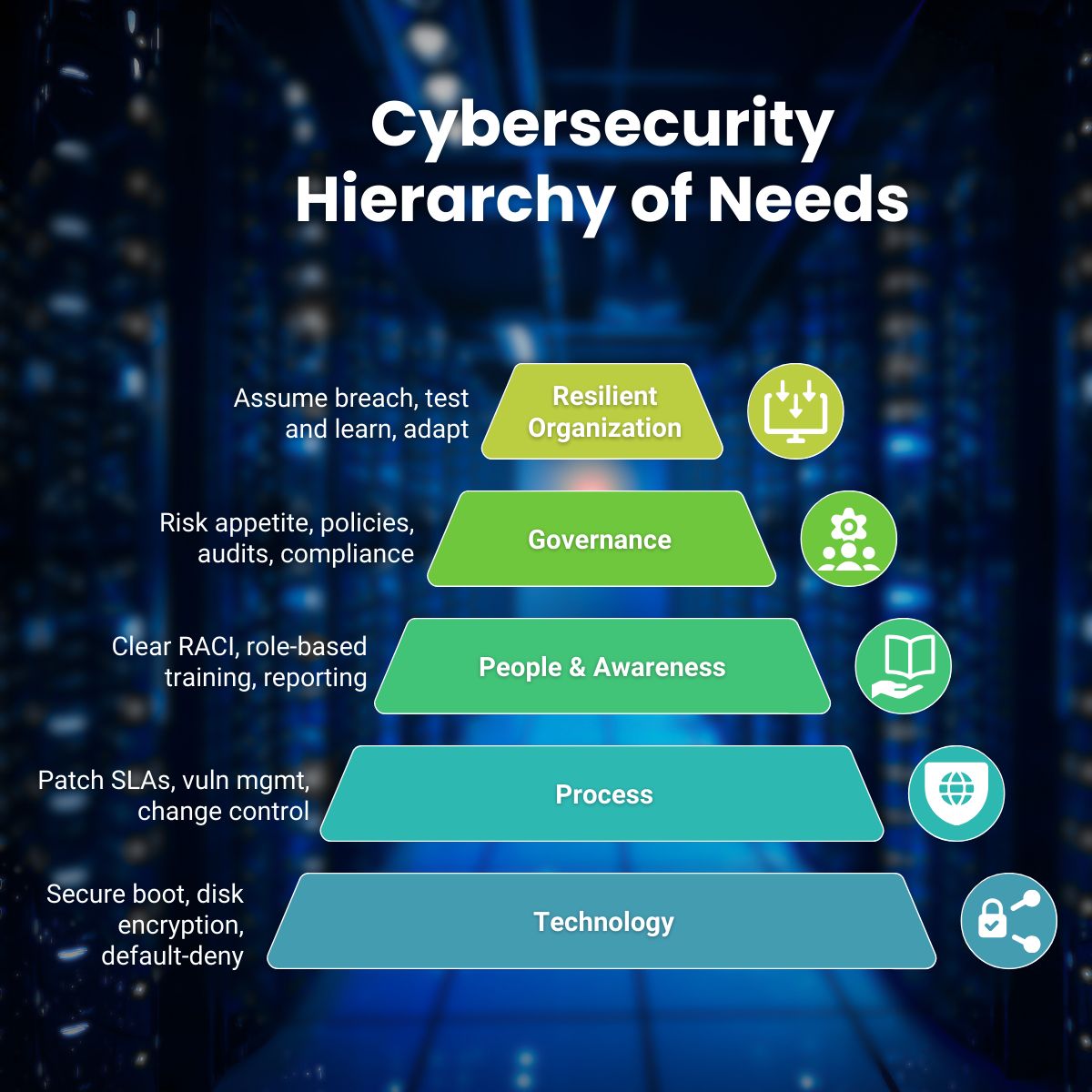
The Maslow Hierarchy of Cybersecurity
Just like in Maslow's original model, the lower levels form the foundation for everything above. Without a stable base, you can invest all you want in advanced technologies, but success will remain elusive.
1. Technology as Foundation: Reliability Before Innovation
The lowest level consists of technology. This isn't about the latest AI-powered threat intelligence platforms, but about the basics: Are your core protections reliable and always on?
Concretely, this means:
- Does your firewall run continuously without gaps?
- Are patches deployed promptly and reliably?
- Is endpoint protection running on all devices?
- Are backups created automatically and tested regularly?
Many organizations skip this level and invest in highly complex security operations centers while critical servers haven't been patched in months. This is equivalent to trying to build a house on sand.
2. Process as Safety: Creating Reliable Operations
Once the technological foundation is in place, you need processes that ensure security. This level defines rhythms, responsibilities, and thresholds so security work happens predictably and continuously.
Critical questions:
- Are there clear owners for each security domain?
- Are vulnerability scans performed at defined intervals?
- Do documented escalation paths exist for security incidents?
- Are service level agreements defined for critical response times?
Without established processes, you rely on the commitment of individual people. As soon as they leave the company or go on vacation, dangerous gaps emerge.
3. People & Awareness as Culture: The Human Dimension
The third level focuses on people and awareness. Even the best technologies and processes fail when employees don't know how to behave securely or are afraid to report mistakes.
Culture-building measures:
- Clear roles and responsibilities for every employee
- Regular, practical security awareness training
- Blameless reporting: a culture where mistakes can be openly communicated
- Continuous reminders and visual cues in daily work
An employee who accidentally clicks on a phishing link should feel safe reporting it immediately so the IT department can respond. A culture of blame leads to incidents being covered up until it's too late.
4. Governance as Alignment: Strategic Direction
The fourth level is governance, the strategic direction of your cybersecurity. Here you define your risk appetite, establish a few meaningful KPIs, and allocate budget according to the biggest loss drivers.
Governance in practice:
- Documented risk tolerance for different business units
- Focus on 5-7 central metrics instead of 50 dashboard indicators
- Budget allocation based on quantified loss scenarios
- Regular review cycles with decision-makers
Many CISOs drown in reporting obligations and create extensive reports that nobody reads. Effective governance focuses on a few business-relevant metrics that actually influence decisions.
5. Resilience as Outcome: The Master Discipline
At the top of the pyramid sits resilience, the ultimate goal. Resilience means assuming that a breach will occur, and continuously testing, learning, and adapting until you achieve your targets.
Building resilience:
- Regular incident response exercises and tabletop drills
- Post-mortem analyses after every incident or exercise
- Continuous improvement based on lessons learned
- Measurable recovery time and recovery point objectives
Can you detect an attack in minutes during an exercise, isolate affected systems, and restore normal operations within hours? If not, your pyramid isn't fully built.
The Provocation for Leaders: Stop Collecting Tools Like Trophies
The central message is uncomfortable but true: Stop collecting security tools like trophies in a display case. Instead, you should deliver provable outcomes.
The critical questions for your leadership team:
- Can you detect a simulated attack in minutes?
- Can you isolate compromised systems in minutes?
- Can you restore operations in hours?
If you cannot answer these questions with "yes" during regular drills, your security pyramid isn't stably built. Your budget should follow the biggest loss drivers, not the shiniest product brochures.
Practical Implementation: The Way Up
Step 1: Audit Your Current Position Honestly assess which level your organization stands on. Do you have the basics under control, or are you investing in advanced threat protection while your patch management processes don't work?
Step 2: Prioritize by Pyramid Levels Invest first in the lower levels. Every dollar that flows into level 5 (resilience) while level 1 (technology basics) is shaky is wasted.
Step 3: Define Measurable Goals For each level, you need concrete, measurable targets. Not "better security," but "99.9% uptime for endpoint protection" or "incident response time under 15 minutes."
Step 4: Continuous Testing Schedule quarterly exercises that stress-test your entire pyramid. Only then will you identify weaknesses before a real attacker exploits them.
Real-World Application: From Theory to Practice
Consider a mid-sized manufacturing company that approached me last year. They had invested heavily in a state-of-the-art SIEM system (level 4-5 technology) but struggled with basic asset inventory (level 1). During a tabletop exercise, they discovered they couldn't even identify which systems to isolate because their asset database was six months out of date.
We restructured their security program to follow the pyramid:
- Month 1-3: Automated asset discovery and baseline hardening
- Month 4-6: Documented processes for patch management and incident response
- Month 7-9: Role-based security training and blameless reporting culture
- Month 10-12: Risk-based KPIs and executive dashboards
- Ongoing: Quarterly resilience testing and continuous improvement
Within a year, their mean time to detect dropped from days to under 30 minutes, and mean time to respond from weeks to under 4 hours.
Common Pitfalls and How to Avoid Them
Pitfall 1: Tool Fetishism Symptoms: Your security team spends more time managing tools than analyzing threats. You have multiple products doing the same job. Solution: Conduct a tool rationalization exercise. If a tool doesn't map to a specific loss driver or compliance requirement, eliminate it.
Pitfall 2: Process Theater Symptoms: You have extensive documentation that nobody follows. Processes exist on paper but not in practice. Solution: Test every process quarterly. If people can't execute it under pressure, simplify it.
Pitfall 3: Awareness Fatigue Symptoms: Annual training completion rates are high, but simulated phishing exercises show no improvement. Solution: Move from annual training to continuous micro-learning with immediate feedback.
Pitfall 4: Vanity Metrics Symptoms: Your reports show hundreds of metrics, but executives can't articulate your security posture. Solution: Identify the 5 metrics that directly correlate with business risk and report only those.
The Business Case: ROI of Pyramid Thinking
Traditional security spending often yields diminishing returns because it addresses symptoms rather than root causes. By following the pyramid approach:
Measurable benefits include:
- Reduced incident frequency: Strong foundations prevent 80% of common attacks
- Faster recovery: Tested processes cut recovery time by 60-75%
- Lower insurance premiums: Demonstrated resilience qualifies for better rates
- Regulatory confidence: Auditors reward systematic approaches
- Talent retention: Security professionals prefer working in well-structured programs
One financial services client reduced their annual security spending by 23% while improving their detection and response capabilities by implementing pyramid-based prioritization. They eliminated redundant tools and reinvested savings in process automation and training.
Conclusion: Successful Cybersecurity Is an Architecture Question
Maslow's hierarchy teaches us a timeless truth: higher goals are only achievable when basic needs are met. In cybersecurity, this means that no matter how advanced your threat intelligence platform is, it won't protect you if your fundamental controls are missing.
The most successful security organizations aren't those with the most tools, but those with the most stable foundation. They build systematically from bottom to top, continuously measure their capabilities, and invest where the greatest risks lurk.
Start today with an honest assessment: Which level of the pyramid does your organization truly stand on? And what is the next concrete step to climb one level higher?
Cybersecurity is not a sprint to the newest tools, but a methodical ascent through all levels of the security pyramid.
